Third-Party
Risk Management
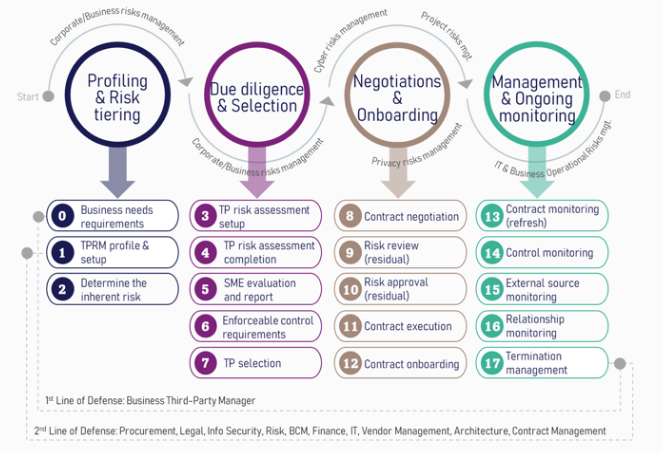
Securing trust between companies and customers as well as meeting regulatory compliance have now become the uttermost priority of businesses. To maintain a sound security posture, organisations need to assess the vendor ecosystem to ensure that risks of cybersecurity, privacy breach, ethics and compliance are mitigated and environmental, social, and governance goals are achieved.
Reduce Compliance and regulatory pressures
Enforce GDPR requirements
Manage multiple parties
Clear-cut onboarding workflows, assessment processes, and risks
Improve visibility into Third-Party risk
Inculcate Third Party code of conduct
Align audit reports to SOC 2 standards
Produce insightful reports to Business and Board members

Third-party risks
assessment
Evaluate third parties’ security controls, leveraging our deep understanding and unparalleled skill set to ensure that third parties’ systems and processes are robust, compliant, and secure

Supply chain privacy
compliance reviews
Assist with contract reviews, establishing the required supply chain practices and conducting third party privacy reviews as per the defined role of data controllers and data processes (privacy data flow analysis, supply chain analysis and vendor reviews) across the supply chain and related risks management

Third Party Risk Management (TPRM) framework
Improve the risk management capabilities of your third parties to improve the security of the Internet
Identify and centrally manage all vendors in a single platform